Partnerships
A Little Help From the Community: How Peloton Works with Security Experts
By: Adrian Stone, VP, Head of Global Information Security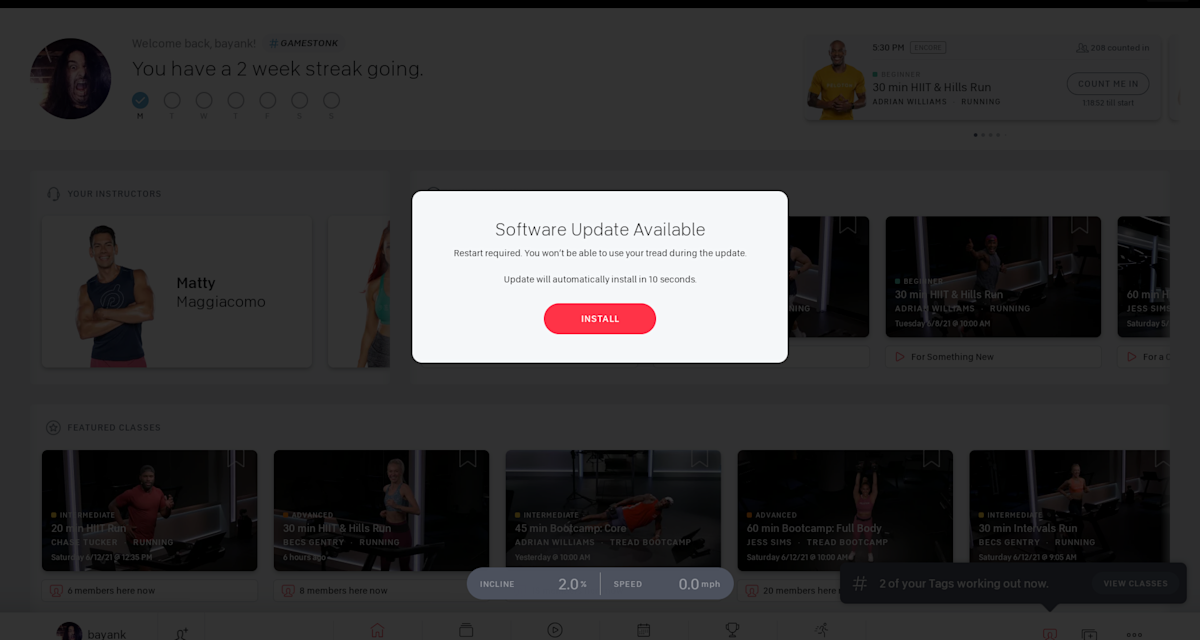
At Peloton, we’re always talking about our community and our Members. And with good reason. Staying in touch with our community is one of the ways we make sure we’re always delivering new experiences and features. We think about the external security community in the same way. The cyber security landscape is constantly changing and it’s helpful for us to maintain close and productive relationships with researchers and other security experts to share knowledge, best practices, or sometimes, just to find someone who can appreciate the nuances and challenges of executing a robust security engineering program. Keeping in touch with the external security community is one of the ways Peloton invests in the security of our products.
Over time, it is not uncommon for attackers to exploit previously unknown security issues. To account for this, a key part of our secure development strategy includes working closely with external security researchers. When they find something that is of potential concern, we want to hear about it. Ultimately, we work together to ensure that our Members and their data are secure, and we provide security updates for newly discovered issues before attackers can exploit them. This industry accepted practice is commonly referred to as Coordinated Vulnerability Disclosure, and more details about our program are available here.
Community in action
A recent example of this process involves a reported issue that we have already fixed. This issue was sent to us by McAfee’s Advanced Threat Research team. They uncovered a security issue where an attacker with physical access to a Peloton Bike+ or a Peloton Tread could ultimately take control of the device. The issue reported to us by McAfee requires that an attacker be able to connect directly to one of the USB ports on the tablet on the Bike+ or the Tread. They would then be able to modify the software on the device, and could then install malware or access data that is communicated between the device and our services. Like with any connected device in the home, if an attacker is able to gain physical access to it, the need for additional physical controls and safeguards becomes increasingly important.

The update that fixes the issue has already been distributed via a mandatory software update. If you own a Bike+ or a Tread*, we recommend that you log into the tablet on your device. If you’re not already on the latest software, you will be immediately required to update your software upon logging in. After updating, your device will be protected against the vulnerability that McAfee reported. If you’re not sure whether you’re on the latest software version, you can check by following the instructions here.
We thank Sam Quinn and Mark Bereza from McAfee Advanced Threat Research for reporting the issue they discovered to us, and for keeping it confidential to help keep our Members safe until we implemented a fix. This kind of collaboration is essential and is part of a healthy security ecosystem between vendors and the research community. We look forward to future opportunities to collaborate like this to ensure that your experience with Peloton continues to be safe and secure.
If you are a researcher and have identified a potential vulnerability, we would like to know about it! You can find the information for our CVD program here.
*Please note that Peloton announced a voluntary recall of the Peloton Tread in partnership with the Consumer Product Safety Commission on May 5, 2021. For more information, click here.